5 Reasons to change IT Support Companies and is beneficial to your Company
Certainly, here are five common reasons why companies might choose to change their IT support companies:
1. Poor Service Quality: If the current IT support company consistently delivers poor service, slow response times, or inadequate issue resolution, it can disrupt the company's operations and hinder productivity. Switching to a company that provides better service can lead to smoother IT operations and improved user satisfaction.
2. Cost Inefficiency: If the current IT support company's pricing structure is no longer cost-effective for the company's budget, or if the company believes they are not getting value for the money they're spending, switching to a more competitively priced provider or one with a more transparent pricing model can lead to cost savings.
3. Technological Obsolescence: Technology is constantly evolving, and if the current IT support company is not keeping up with the latest advancements, it can result in outdated systems, security vulnerabilities, and missed opportunities for innovation. Switching to a provider with a stronger focus on emerging technologies can help the company stay competitive.
4. Security Concerns: If the current IT support company has experienced security breaches or lacks the expertise to effectively address cybersecurity threats, the company's sensitive data and operations could be at risk. Switching to a provider with a robust cybersecurity approach can enhance data protection and reduce the likelihood of security incidents.
5. Lack of Industry Expertise: Certain industries have specific IT requirements, regulations, and compliance standards. If the current IT support company lacks experience or understanding of the company's industry, it can lead to non-compliance, inefficiencies, and missed opportunities. Switching to a provider with industry-specific knowledge can ensure that IT strategies align with the company's industry needs.
Before deciding to switch IT support companies, it's important for a company to thoroughly evaluate its current and future IT needs, and plan for a smooth transition to minimize disruption. Download “The 2023 IT Services Buyer’s Guide” to set expectations and help eliminate frustrations with your new IT support provider.
Embracing Change: Why Switching IT Support Companies is Good for Your Business
I was talking with a potential customer, and she made a comment as to why switch IT support companies because she knows what she has with her current support company despite her frustrations with the lack of direction of provide a technology roadmap for budgeting and expectation setting, response time taking longer, taking a Band-Aid approach to fixing the same problem over and over again, working around the support companies timeframe instead of her employees taking priority, and not knowing if her data is protected. That conversation prompted me to write this article on why making a switch would be beneficial to her company.
In today's fast-paced digital landscape, businesses rely heavily on efficient IT systems to remain competitive where do more with less is resonating with some companies. A reliable and proactive IT support partner is crucial for ensuring seamless operations, data security, and effective troubleshooting. However, over time, businesses may outgrow their existing IT support companies or find themselves facing recurring issues and limitations. Making the decision to change IT support companies can be daunting, but it can bring numerous benefits to your business. Here are six (6) reasons why switching IT support companies can be a game-changer for your organization.
1. Fresh Perspective and Innovative Solutions
One of the most significant advantages of changing IT support companies is gaining access to a fresh perspective and innovative solutions while keeping budgets under control. New providers bring a different set of skills, experiences, and knowledge to the table. They can evaluate your existing IT infrastructure with a critical eye and identify areas for improvement. An innovative IT support company will introduce modern technologies and best practices, enhancing your business's efficiency and productivity which are a direct result to company growth.
2. Customized Solutions for Your Business Needs
Every business is unique, and its IT requirements are equally distinctive. Switching IT support companies allows you to find a provider that tailors solutions specifically to your business needs. Rather than receiving generic support, you can work with a company that understands your industry and the challenges you face. This customization ensures that your IT systems align with your business goals and contribute to your long-term success.
3. Increased Security and Data Protection
Data breaches and cyberattacks have become a prevalent threat in the digital age where we are connected 24/7/365 on many digital platforms. As businesses accumulate sensitive customer information and proprietary data, the need for robust cybersecurity measures grows exponentially. By switching to a reputable IT support company, you gain access to enhanced security protocols and expertise in handling cyber threats. They can implement encryption, firewalls, and regular security audits to safeguard your data from potential breaches.
4. Cost-Effectiveness and Scalability
Over time, businesses may experience growth or fluctuations in their IT requirements. A reliable IT support partner can adapt to these changes and offer scalable solutions. By switching IT support companies, you can find a provider that offers cost-effective packages tailored to your budget and requirements. This flexibility ensures that you pay only for the services you need, allowing you to allocate resources efficiently.
5. Improved Response Times and Downtime Reduction
Minimizing downtime is critical for businesses to maintain productivity and prevent revenue loss. A switch in IT support companies can lead to improved response times and quicker issue resolution. A proactive IT support partner will monitor your systems round-the-clock 24/7/365, identifying and addressing potential problems before they escalate. This approach significantly reduces downtime and enhances your business's overall operational efficiency.
6. Focus on Core Business Activities
Managing IT issues internally or dealing with inadequate IT support can be time-consuming and distract your team from focusing on core business activities. Switching to a competent IT support company offloads the burden of IT management from your team, allowing them to concentrate on strategic initiatives and improving customer service, and drives company growth.
I value your feedback, changing IT support companies can be a transformative step for your business. I have embraced change over my years of entrepreneurship because change opens doors to fresh perspectives, innovative solutions, and creates awareness around securing your most valuable asset which is your data. By customizing services to your business's unique needs, you ensure that your IT infrastructure aligns with your growth objectives.
A reliable IT support partner will not only reduce downtime but also offer cost-effective and scalable solutions. This allows you to allocate resources efficiently and focus on driving your business forward. Therefore, it is essential to carefully evaluate your current IT support arrangement and explore opportunities for improvement by embracing change and partnering with an IT support company that truly aligns with your business goals.
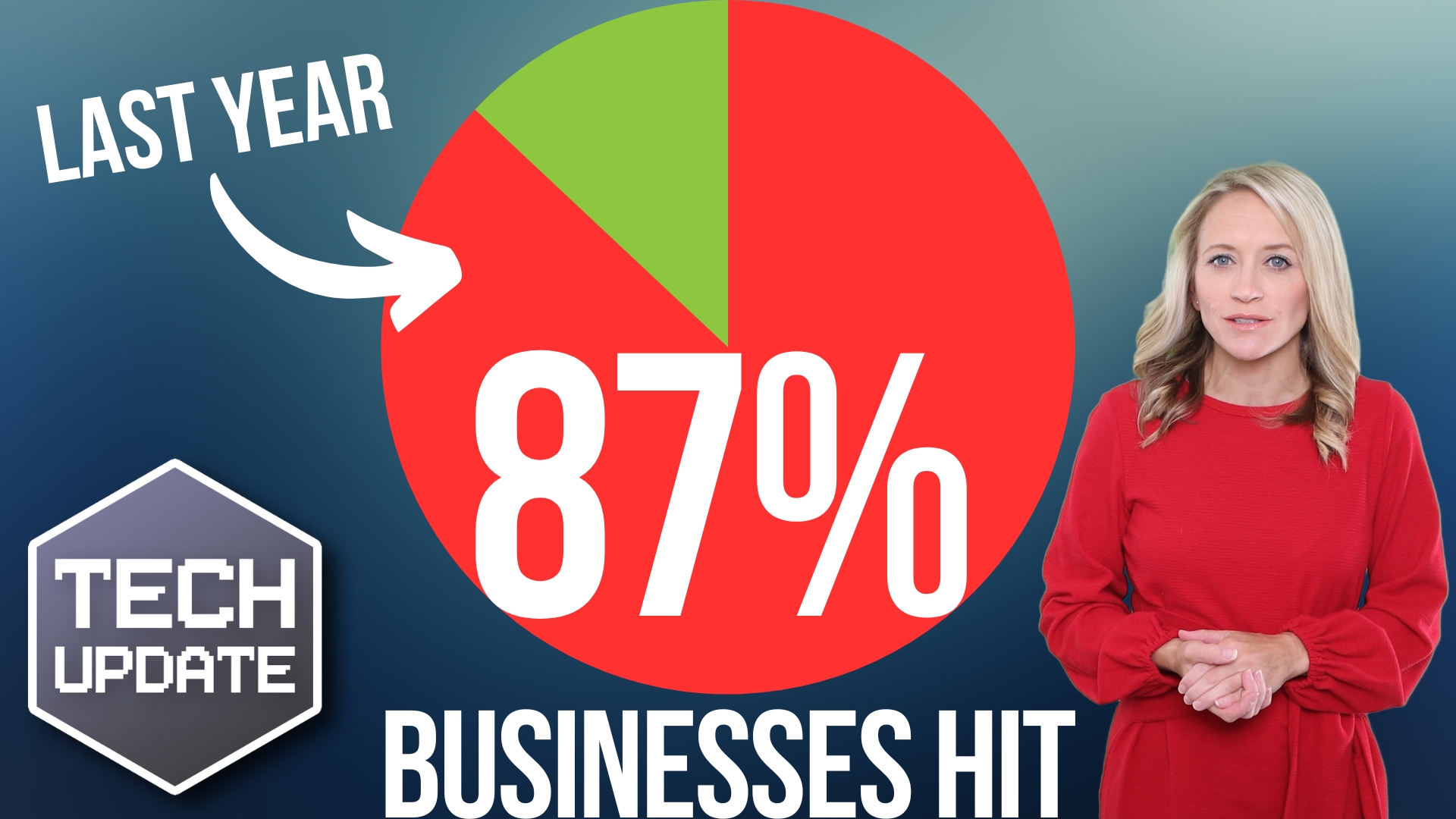
Scary stat: 87% of businesses hit by this in the last year
You may think that cyber attacks only happen to large corporations. But unfortunately, that’s not the case.
According to a recent report, almost two-thirds of small and medium-sized businesses (SMBs) suffered at least one cyber attack over the past year. That’s a staggering number, and it should serve as a wake-up call for businesses everywhere.
But it gets worse.
More and more businesses are also experiencing repeat attacks, with 87% reporting at least two successful attacks over the past year. And on average, a company suffers almost five successful cyber incidents.
Terrifying.
The question is, why are these attacks happening, and what can you do to prevent them?
The most common types of cyber attack that businesses face are malware and ransomware.
Malware is malicious software. It invades your system and can cause all sorts of problems, from slowing down your operations to stealing your data.
Ransomware is even more dangerous as it encrypts your data, making it impossible for you to access it unless you pay a ransom fee. This can be devastating for any business and can lead to significant losses and downtime.
What factors are contributing to more successful attacks?
One reason is the rise in BYOD (Bring Your Own Device). This means employees using their personal devices to access company information, which can be risky.
Another factor is the explosion of productivity apps, which can create security vulnerabilities if not properly secured.
Finally, the number of devices we’re using now means there are more entry points for cyber criminals to exploit.
The good news is that there are steps you can take to protect your business. Here are five solid security steps you can take.
- Use strong passwords: Passwords are your first line of defense, so make sure they’re strong and unique. Better yet, use a password manager that can create and remember randomly generated passwords
- Keep software up to date: Software updates often contain security fixes, so make sure you’re always running the latest version. This applies to both your operating system and all applications you use
- Train your staff: Educate your employees on how to identify phishing emails and other scams. You can also run regular security awareness training sessions to keep everyone up to date
- Backup your data: Doing this means if you do suffer a cyber attack, you can restore your systems quickly and with less disruption
- Use antivirus software: This can help protect your systems from malware and other threats. Make sure you’re running a reputable and up-to-date solution
Remember, prevention is always better than cure. Take action today to help you stay protected.
And if that seems like a lot of extra work, let us help. Get in touch today.
This is the latest trend in phishing attacks
Have you heard the saying, “A picture is worth a thousand words”? It seems cyber criminals have too, and they’re using it to their advantage.
In a new twist on phishing campaigns, cyber criminals are luring victims to click on images rather than downloading malicious files or clicking suspicious links.
Let’s dive into the warning signs, so you can keep your business safe from these sneaky attacks.
First things first, what’s the big deal about clicking on an image? It might be promoting a killer deal or one time offer.
But when you click on the image, you don’t go to the real website. Instead it’s a fake site designed to steal your personal information.
Imagine being lured in by a cute cat photo only to find out that Mr. Whiskers was actually a wolf in sheep’s clothing! Not so cute anymore, right?
So, how can you tell if an image is part of a phishing campaign? Here are some warning signs to look out for:
- Unexpected emails: Did you receive an email from someone you don’t know or weren’t expecting? Be cautious! It’s like accepting candy from a stranger – you never know what you’re getting yourself into.
- Too good to be true: If an email promises you a free vacation or a million dollars just for clicking on an image, remember the golden rule: if it sounds too good to be true, it probably is.
- Spelling and grammar mistakes: We all make typos, but if an email is riddled with errors, it could be a sign that something is going on.
- Mismatched logos or branding: If an email claims to be from a reputable company but the logo or branding doesn’t match up, assume it’s a scam.
Now that you know what to look for, let’s talk about how to protect your business from these image-based phishing attacks:
- Educate your employees: Knowledge is power! Make sure your team is aware of the latest phishing tactics and knows how to spot the warning signs.
- Keep software up-to-date: Just like you wouldn’t drive a car with bald tires, don’t let your software become outdated. Regular updates help patch security vulnerabilities that cyber criminals might exploit.
- Use strong passwords: It might be tempting to use “password123” for all your accounts, but resist the urge! A strong, unique password for each account can help prevent unauthorized access. Using a password manager is even better.
- Enable multi-factor authentication (MFA): MFA adds an extra layer of security by requiring people to verify their identity through another method, such as a text message or fingerprint scan.
- Backup your data: In case disaster strikes, make sure you have a backup of all your files. That way, you won’t be left high and dry if your data is compromised.
Whilst cyber criminals are getting smarter and smarter with their tactics, there’s no need to panic. By being aware of the warning signs and taking proactive steps to protect your business, you can stay one step ahead of these digital tricksters.
Remember, not all that glitters is gold – or in this case, not every cute cat picture is just a cute cat picture. Stay vigilant, and don’t let the scammers win!
Privacy alert: Change this setting in Edge, now
UPDATE: This controversial image enhancement feature now seems to have been removed by Microsoft, following privacy concerns.
Don’t be mistaken, we love Microsoft Edge (and think you will too), but lately, something has come to our attention that we wanted to share.
It’s always a good idea to be aware of what your browser is doing behind the scenes. And there’s an Edge setting that you might be interested to learn about. It’s one that sends the images you view online to Microsoft.
While this might not seem like a big deal on the surface – it’s done to enhance the images – some business owners might be concerned about the privacy implications. After all, you never know who might be looking at your browsing history.
The good news is that it’s easy to disable this setting if you’re concerned about it. Here’s how:
- Open Microsoft Edge and click on the three dots (“More actions”) in the upper-right corner of the screen
- Select “Settings” from the drop-down menu
- Scroll down and click on “Privacy, search, and services”
- Under the “Services” section, turn off the toggle switch next to “Improve your web experience by allowing Microsoft to use information about websites you browse to improve search suggestions, or to show you more relevant advertizing”
- That’s it! With just a few clicks, you’ve disabled the feature that sends images to Microsoft.
Of course, there are other settings in Edge that you might want to explore as well. Like the ones that control your data collection preferences, or the ones that limit pop-ups and redirects.
Why should you take a few minutes to check out your browser settings? Well, for one thing, it can help protect your privacy and security online. By being aware of what your browser is doing, you can make informed decisions about what data to share (and what to keep private).
Plus, exploring your browser settings can be a fun and educational experience in its own right. You might discover new features or hidden gems you never knew existed.
And don’t worry, you don’t have to be a tech expert to understand these settings. In fact, Microsoft has done a great job of making them simple and straightforward, with clear explanations and helpful tips along the way.
If you ever get stuck, our team is happy to help. Get in touch.
Browse with confidence: Microsoft Edge’s security boost
Browsing the web can be risky. It only takes one click on one bad link to put your business’s data at risk.
With cyber criminals constantly targeting businesses using automated tools, it’s important to stay one step ahead with your online security.
That’s why we’re excited that Microsoft is working on a major security update for its Edge browser, which will bring enhanced security to everyone using it.
It’s adding new security features and beefing up existing ones.
Maybe you’ve already seen features such as Password Monitor. This alerts you if any of your saved passwords have been compromised in a data breach, prompting you to change them immediately.
There’s also SmartScreen technology, which will help safeguard you from phishing scams and malware.
This checks websites against a list of known malicious sites, as well as analyzing URLs for any suspicious patterns or characteristics. If it detects something that’s not right, you’ll be warned before you proceed to the site.
Why should you care about all these security updates?
It comes down to this: Using a less secure browser could leave you vulnerable to all sorts of online threats. Cyber criminals are constantly coming up with new ways to exploit weaknesses in software, so it’s important to stay up-to-date with the latest security measures.
Plus, let’s face it – no one wants to deal with the aftermath of a cyber attack. Whether it’s dealing with financial losses, identity theft, or just the hassle of cleaning up the mess, the consequences of a breach can be far-reaching.
By using a secure browser like Edge, you can reduce your risk of falling victim to such attacks.
Of course, we know that not everyone is an expert on cyber security. That’s why Microsoft is making it easy to stay safe without needing a degree in computer science.
The new security features are built-in and easy to use so you don’t have to worry about configuring anything yourself. You can browse the web with peace of mind.
If you’re not already using Edge, give it a go. And if you need help getting your 365 suite optimized for your business, get in touch.
What to Look for in an Outsourced IT Partner
In today’s digital age, most businesses rely heavily on technology to streamline their operations and stay ahead of the competition. However, managing an entire IT infrastructure in-house can be overwhelming and costly.
That’s where outsourcing IT services comes into play. By partnering with a reliable and efficient outsourced IT provider, you can offload the complexities of managing your technology infrastructure and focus on your core objectives.
However, with a myriad of IT service providers in the market, how can you ensure that you choose the right one for your business? In this blog, we’ll take you through a few important things you should consider when browsing for an outsourced IT partner. By clearly understanding what to look for, you can make an informed decision and find a partner that aligns with your organization’s goals and requirements.
Factors to consider
Here are a few key factors to keep in mind before you commit to an IT partner:
Cultural alignment
Choosing an IT service provider that aligns closely with your organization’s culture is crucial for a successful partnership. Cultural alignment means the IT service provider shares values, work ethics and communication styles with your business.
With a strong cultural fit, the collaboration becomes seamless and both parties can work together more effectively. This alignment enhances communication, trust and mutual understanding, leading to smoother project implementation and better results.
By selecting an IT service provider that understands and respects your organizational culture, you can foster a productive working relationship and achieve your IT objectives more efficiently.
Vested interest and industry knowledge
A reliable IT service provider should demonstrate a vested interest in your organization’s success. This means they are genuinely invested in building a long-term partnership and are committed to understanding your business goals and challenges.
The IT service provider should also possess industry knowledge and experience relevant to your specific sector. This understanding allows them to provide tailor-made IT solutions that address your unique needs.
By partnering with an IT service provider with a genuine interest in your success and industry expertise, you can benefit from their insights, strategic guidance and proactive support. Their knowledge of industry best practices can help you navigate technological advancements and make informed decisions that drive your business forward.
References and value demonstration
When evaluating potential IT service providers, it is essential to seek references and ask for evidence of the value they have provided to their clients. Speaking with their current or past clients allows you to gain valuable insights into their performance, reliability and customer satisfaction.
Requesting real metrics and use cases enables you to assess the IT service provider’s track record and evaluate how their services have benefited other businesses. This information gives you confidence in their capabilities and helps you gauge their suitability for your organization.
By choosing an IT service provider with positive references and a demonstrated ability to deliver value, you can minimize risks and make an informed decision that aligns with your business goals.
Round-the-clock service
Technology disruptions can occur anytime, and prompt resolution of IT issues is crucial to minimize downtime and maintain business continuity.
An IT service provider offering round-the-clock service ensures that technical support and assistance are available whenever needed. This 24/7 support can be crucial if you operate across different time zones or have critical operations outside regular business hours.
By partnering with an IT service provider that provides continuous support, you can have peace of mind knowing that any IT issues will be addressed promptly, reducing the impact on your operations and enabling your business to run smoothly without interruption.
Act before it’s too late
Ready to find the perfect IT service provider for your business? Don’t wait any longer — reach out to us today and schedule a no-obligation consultation. Our team of experts is eager to understand your unique needs and discuss how our services can help your organization thrive.
To take control of your technology infrastructure and ensure it aligns with your business goals, download our complimentary checklist “Top Warning Signs Your Technology Is Holding Your Business Back.” This resource will provide you with valuable insights on the primary tech red flags to keep an eye on. Empower yourself with the knowledge needed to make an informed decision.
Don’t Let These Outsourced IT Myths Limit Your Success
In today’s fast-paced and digitally driven world, the demands placed on the IT infrastructure of businesses like yours are ever-increasing. To meet these challenges head-on, embracing outsourced IT services and entrusting your technological needs to an expert third-party provider is the best option. By partnering with these specialists, you can tap into a wealth of knowledge, experience and cutting-edge technologies that might otherwise be challenging to obtain in-house.
Outsourced IT acts as a beacon of relief, enabling you to offload the burdensome responsibilities of managing IT. With dedicated professionals and advanced tools at their disposal, outsourced IT providers can implement robust security measures, ensure seamless data backups and monitor systems 24/7, all while adhering to industry best practices and compliance standards.
However, amid the promise and potential of outsourced IT, lingering myths can hold you back from embracing this transformative approach. In this blog, we’ll dispel the popular myths and shed light on the truths related to outsourced IT.
Debunking common outsourced IT myths
Without further ado, let’s debunk the myths so you can get the most out of outsourced IT:
Myth #1: It only focuses on technical issues.
Contrary to popular belief, outsourced IT encompasses much more than just technical support. It goes beyond resolving everyday glitches and delves into critical areas that drive business success.
Leading IT service providers offer comprehensive and advanced solutions, including robust cybersecurity measures, reliable backup and recovery systems, and efficient cloud computing services.
By partnering with a trusted IT service provider, you gain a strategic ally who aligns technology with your unique needs, boosts productivity and offers proactive support.
Myth #2: It’s only for large enterprise companies.
The truth is that businesses of all sizes and across industries can benefit immensely from outsourcing their IT needs. Even smaller organizations, often constrained by limited resources, can gain a lot.
By partnering with a committed IT service provider capable of handling diverse technological demands, you can tap into their resource pool rather than struggling to build and maintain an in-house IT team. This allows you to gain an edge over the competition.
Myth #3: It’s too expensive for my budget and resources.
Cost considerations often fuel doubts about outsourced IT. However, when carefully evaluated, outsourcing proves to be a cost-effective solution.
Investing in an internal IT department entails substantial expenses, ranging from recruitment and training to salaries and benefits. On top of that, the ever-evolving technology landscape demands constant investments in infrastructure upgrades and software licenses.
Outsourcing IT services provides access to specialized expertise and eliminates the financial burden of maintaining an internal team. With economies of scale at play, you can access cutting-edge infrastructure and security measures at a fraction of the cost.
Myth #4: It leads to a loss of control over IT operations.
A common fear associated with outsourced IT is the perceived loss of control. However, the reality couldn’t be further from the truth.
By partnering with the right IT service provider, you gain enhanced visibility into your IT operations, leading to better decision-making and outcomes. Detailed reports, analytics and performance metrics offer valuable insights that empower you to align your IT strategies with your objectives. Moreover, a collaborative relationship with the IT provider fosters transparency, open communication and meaningful decision-making.
Partner for success
Ready to revolutionize your business with the remarkable benefits of outsourcing your IT operations? Look no further! Get in touch with us today and embark on a transformative journey toward streamlined efficiency and accelerated growth.
We know managing your IT infrastructure can be complex and time-consuming, diverting your attention away from your core business objectives. That’s where our expertise comes into play — armed with extensive experience and cutting-edge solutions to seamlessly handle all your IT needs.
We’ve created a comprehensive infographic that highlights the undeniable advantages of outsourced IT. Learn how it can transform your business and propel you ahead of the competition. Click here to explore the power of outsourcing.
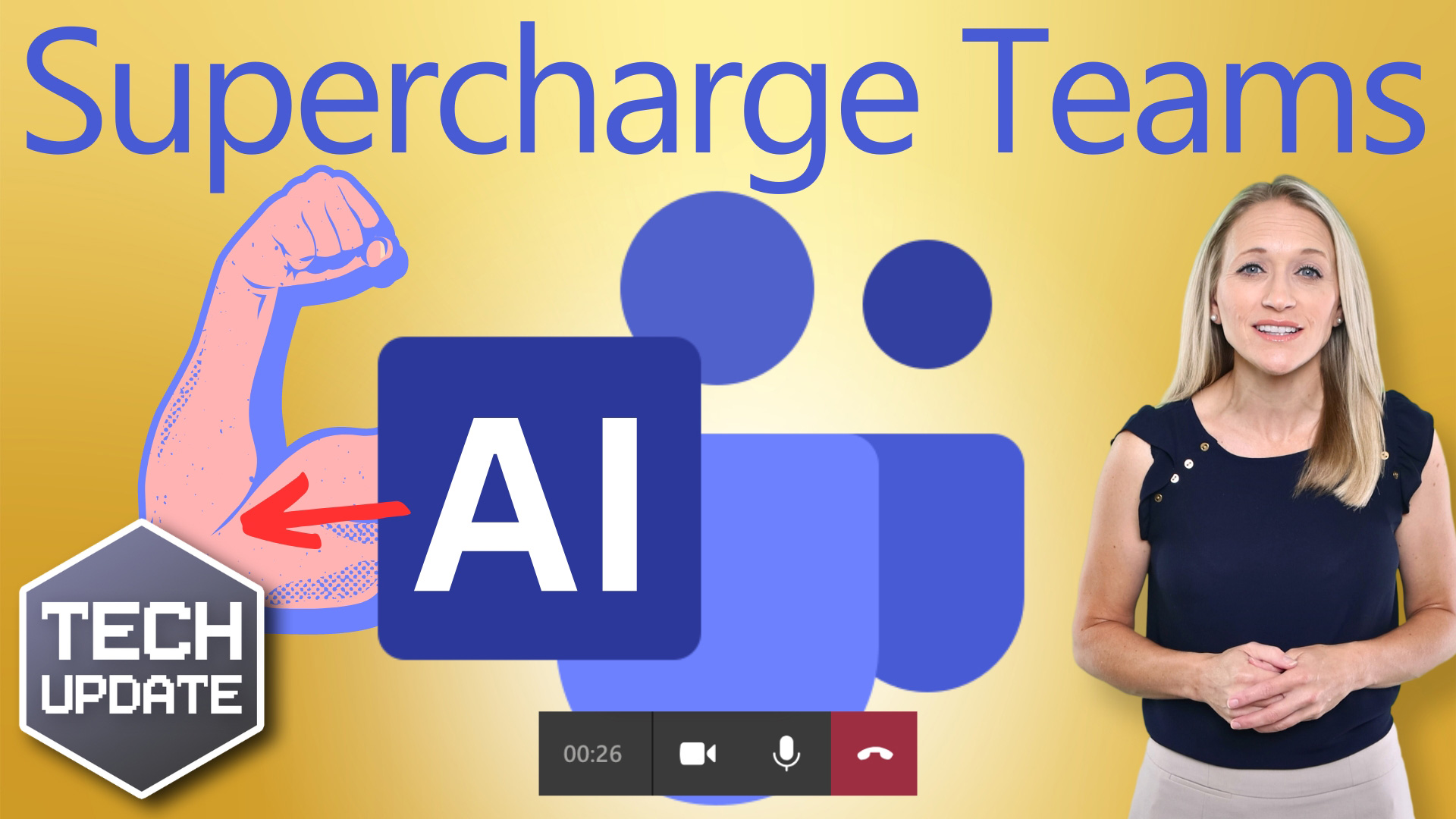
Now AI can make your Teams meetings more productive
Are you tired of wasting precious time in meetings, only to leave feeling confused and disorganized?
Do you struggle to keep track of all the action items and follow-up tasks that come out of these meetings?
Microsoft Teams has launched a new feature which could solve your problems and boost productivity.
Meeting Recap is an AI-based intelligent meeting recap feature, available exclusively to Teams Premium subscribers. This innovative feature harnesses the latest in artificial intelligence technology to generate comprehensive summaries of your meetings.
That means no more tedious recaps… but hello to accurate and efficient summaries that capture all the key points from your meetings.
The Meeting Recap feature doesn’t stop there. It automatically identifies action items and follow-up tasks, assigns them to team members, and even sets deadlines for completion. This means that everyone involved in the meeting knows exactly what they need to do and when it needs to be done. A great way to improve communication and collaboration within your team.
But it’s not just about efficiency. The meeting recap feature also offers customizable options to tailor the feature to your specific needs. Choose what information is included in the summary to ensure that you receive the most relevant and useful information possible.
If you’re not a Teams Premium subscriber, are there benefits of investing in this new feature?
Yes! For starters, it streamlines your workflow, saving you both time and money.
You don’t have to waste hours trying to decipher meeting notes and action items. Instead, you’ll have access to a clear and concise summary that you can refer back to any time.
Additionally, it improves organization and accountability within your team. With assigned action items and deadlines, everyone knows exactly what is expected of them.
Don’t underestimate the power of this new Meeting Recap – it’s a game-changer for businesses that want to increase productivity.
Don’t wait. If you need help upgrading to Teams Premium, we’re here for you. Get in touch.
Stop! And think, before you act on that email
How many times a day do you respond to an email without really thinking about its contents?
Maybe it’s a request for some information. Perhaps it’s asking you to pay an invoice. All mundane stuff. But no sooner than you’ve hit send, you’ve fallen victim to a Business Email Compromise (BEC) attack.
A BEC attack occurs when a cyber criminal gains access to your business email account and uses it to trick your employees, customers, or partners into sending them money or sensitive information. They do this by impersonating someone senior, and abusing their position of trust.
It might sound like something that only happens to big corporations, but that’s not the case.
According to the FBI, small and medium-sized businesses are just as vulnerable to BEC attacks as larger ones. In fact, these attacks have cost businesses more than $26 billion over the past few years.
And Microsoft brings more bad news, with its recent findings showing that they’re getting both more destructive and harder to detect.
So, what can you do to protect your business from BEC attacks? Here’s our advice:
- Educate your employees: They are the first line of defense against BEC attacks. They need to know how to spot phishing emails, suspicious requests, and fake invoices. Train them regularly on cyber security best practice, like strong passwords, multi-factor authentication, and secure file sharing.
- Use advanced email security solutions: Basic email protections like antispam and antivirus software are no longer enough to block BEC attacks. You need more advanced solutions that use artificial intelligence and machine learning to detect and prevent these attacks in real-time. Look for email security providers that offer features like domain-based message authentication, reporting, and conformance (DMARC), sender policy framework (SPF), and DomainKeys Identified Mail (DKIM).
- Set up transaction verification procedures: Before transferring funds or sensitive information, establish a verification process that confirms the authenticity of the request. This could include a phone call, video conference, or face-to-face meeting. Don’t rely on email alone to confirm these types of requests.
- Monitor your email traffic: Regularly monitor your email traffic for anomalies and unusual patterns. Look for signs like unknown senders, unusual login locations, changes to email settings or forwarding rules, and unexpected emails. Make sure you have a clear protocol in place for reporting and responding to any suspicious activity.
- Keep your software up to date: Ensure that you’re always running the latest version of your operating system, email software, and other software applications. These updates often include vital security patches that address known vulnerabilities.
BEC attacks are becoming more common and more sophisticated, but with the right awareness, training, and security solutions, you can protect your business.
Don’t wait until it’s too late – take action today to keep your business safe.
If you want to know more about how to protect your business from cyber threats, our team is always ready to help you. Give us a call.
Is your business data at risk? Don’t take chances with old tech
When you replace old computers or external drives, do you delete data and then just… get rid of them?
You could be putting your sensitive data at risk.
A new study by a data recovery specialist shows that millions of deleted files can be recovered from improperly wiped hard drives that are sold online.
It’s not just buyers who can access your old files. Cyber criminals often buy used hard drives and attempt to recover data from them. This could include anything from confidential business information to client details.
It’s easy to forget about old data when you’re excited about shiny new technology. However, it’s important to consider what’s on that old drive before selling it or disposing of it.
Even if the drive is encrypted, it’s still possible for data to be recovered. And if the drive is damaged, there’s a chance that some of the data is still salvageable. It’s better to be safe than sorry when it comes to sensitive information.
Think about it this way: Would you leave important documents lying around for anyone to see? Of course not! Your digital information deserves the same level of protection.
So what can you do to protect yourself?
Don’t let your old hard drives become a liability. Take the time to have them properly wiped or destroyed before disposal. If you’re upgrading hardware, consider hiring a professional to handle the data transfer and ensure that your old devices are wiped clean.
This isn’t just about protecting yourself. It’s about protecting your employees, clients, and anyone else whose personal information you may have stored on that old drive.
It’s a small investment to make for the peace of mind that comes with knowing your data is safe from prying eyes.
Don’t take chances with your data – take action to protect it:
- Properly wipe or destroy old hard drives
- Bring in a professional for your hardware upgrades
- Upgrade your overall security practices
Published with permission from Your Tech Updates.
How to Stay Ahead of AI-Powered Cybersecurity Risks
While artificial intelligence (AI) has many benefits for businesses, it has also created new vulnerabilities that cybercriminals can exploit to carry out complex cyberattacks that are difficult to detect and mitigate. Using AI, hackers can create convincing phishing emails that bypass spam filters. Similarly, cybercriminals can leverage AI to manipulate security systems and gain unauthorized access that causes irreparable damage to your business and your reputation.
This emerging threat landscape can be tough for businesses that do not have a dedicated IT security team equipped with the advanced tools to mitigate complex cybercrimes. Fortunately, there is a lot you can do to bolster your organization’s cybersecurity. In this blog, we'll explore ways to improve your preparedness against AI-powered cyberattacks.
Security best practices for AI
Here are some practical tips for enhancing your organization's cybersecurity posture against emerging AI threats:
- Provide continuous, real-time cybersecurity training for your team
AI technology is evolving quicker than ever, and so are cyberthreats. Mix the two together without continuous cybersecurity training for your team and you’ll have a security disaster on your hands.
When a hacker targets an organization, an employee often gets blamed for clicking the wrong link or downloading an infected file. However, rather than blaming an individual, devise a strategy to ensure all your employees have the knowledge and training they need to make the right decisions.
For example, you can use real-time scenarios or simulations to help your employees identify phishing emails so they don’t fall for malicious attempts. You can even set up regular, ongoing security awareness training to educate your employees about persistent threats like ransomware and social engineering attacks. By making cybersecurity training an essential part of your work culture, you can have all your employees invested in organizational security.
- Improve security policies and enforce them
As AI-powered cyberthreats evolve, take proactive steps to improve cybersecurity policies and enforce them rigorously through consistent communication that emphasizes the necessity of good cyber hygiene. Your IT and HR teams can also work on cybersecurity strategies and policies that ensure your employees stay vigilant and aware of the latest AI cyberthreats. For example, you can have weekly newsletters sent out to employees to keep them updated on emerging threats.
Additionally, you can carry out regular risk assessments and implement multifactor authentication to enhance your cybersecurity. Businesses that don’t have IT teams or security resources have been able to build a strong IT security stance with the help of a trusted IT service provider.
- Partner with an IT service provider
An experienced IT service provider will have the inside scoop on all the latest developments in AI and can help you build a formidable cybersecurity posture that protects your business from AI-related threats. Since an IT service provider has the advanced resources and tools to combat threats, you can focus on crucial business decisions without having to worry about managing your IT security.
We are here to help
Make cybercriminals the least of your worries. Consider partnering with an IT service provider like us. We have the experience and expertise to help you build a solid cybersecurity posture against AI-fueled security threats without breaking the bank. Contact us today!
Download our infographic, "The Business Leader's Roadmap to AI Success" and discover countless ways AI can improve your business productivity and profitability.