How to Successfully Leverage AI in Your Business
Artificial intelligence (AI) can help organizations like yours gain an edge in today's highly competitive business landscape by increasing efficiency, productivity and profitability. You can improve customer service, enhance marketing efforts, optimize inventory management, streamline sales processes and more.
Implementing AI requires a strategic approach to ensure that it delivers the intended benefits while being practical, ethical and aligned with the overall business plan of your organization. In this blog, we'll explore the best practices you can implement to successfully integrate AI into your business.
Best practices for leveraging AI successfully
- Pick the best places to start
Identify critical business areas that AI can solve or add value to. By prioritizing key functions to automate and optimize, you can achieve a quick win and prove the value of AI integration to stakeholders.
- Ensure data quality and integrity
For the success of your AI strategy, your data must be clean, structured and complete. This will help your AI model deliver more accurate and valuable insights that improve the efficiency of your business processes and decision-making.
- Be open to innovation and experimentation
AI technology is rapidly expanding, and the best way your business can truly reap the rewards of AI is by staying open to innovation and experimentation. By adopting new approaches and opportunities to innovate, you can find new ways to leverage the full potential of AI technology.
- Get help and support from the experts
Transitioning to a new technology on your own can be challenging. That's why you should consider partnering with an IT service provider like us to access the expertise and tools you need to ensure you implement best practices as per industry standards.
- Think about the ethics
For the long-term success of your business, it’s crucial to use AI ethically and transparently, with clear accountability measures in place. Ensure that you use unbiased data and maintain transparency in the algorithm from the beginning. This will minimize risks and ethical challenges from popping up down the road.
Wondering how to get started?
Figuring out where AI can fit within your business can be challenging. We can show you the right strategies to make AI implementation a breeze. Contact us today to get started!
Download our checklist, "Four Key Actions to Harness the Power of AI in Your Business" to learn how to overcome potential obstacles and get all the benefits of AI for your business.
Here’s how cyber criminals try to hack your accounts while you sleep
Have you ever felt frustrated by the flood of notifications from your multi-factor authentication (MFA) app?
Well, cyber criminals have too. And they’re taking advantage of “MFA fatigue” to try to gain access to your sensitive business data.
MFA is essential for keeping your data secure. It adds an extra layer of security to your apps and accounts by asking you to verify your identity in two or more ways, such as a password and a code sent to your phone.
The constant alerts can be overwhelming though.
Attackers know this and will bombard employees – sometimes in the middle of the night – with a constant stream of MFA notifications. Which makes it more likely someone will authenticate a login attempt through frustration, tiredness, or just to get the notifications to stop.
But now there’s a new weapon in the fight against MFA fatigue.
Microsoft Authenticator has introduced number matching as a way of making sure your MFA notification is from the correct login attempt, preventing cyber criminals from taking advantage of notification fatigue.
How does number matching work?
When you receive an MFA notification, the app will display a randomly generated number. You then need to input this number to authenticate the login attempt and prove you’re not a cyber criminal trying to access your business data.
That’s not all. Microsoft Authenticator also allows for biometric authentication, which means you can use your face, fingerprint, or other unique physical features to prove your identity and combat the threat of MFA fatigue attacks.
With these security measures in place, your business can stay ahead of cyber criminals and keep your sensitive data better protected.
If you already use Microsoft Authenticator, number matching is ready to use. Simply make sure your app is up-to-date, and you’ll be protected.
If you use another MFA system and want to look at how to make your security better or easier, we can help. Get in touch.
Published with permission from Your Tech Updates.
Don’t Trust These Zero Trust Security Myths
In today’s threat landscape, where businesses are constantly at risk of being targeted by a cyberattack, adopting a zero-trust security model could be a wise decision from a cybersecurity point of view.
Zero trust works on the premise that everything — humans, machines or applications — poses a risk to your network and must prove trustworthy before accessing the organization’s network or data. By insisting on verification and authentication at every step, zero trust makes it difficult for a hacker to gain access through a compromised user account or device.
However, with the increasing relevance of the zero-trust framework, there also has been an increase in misinformation surrounding it, fueled mainly by security vendors vying to sell their miracle solutions. In this blog, we will discuss the top zero-trust myths and how an IT service provider can ease the entire process without you facing any roadblocks.
Top zero-trust myths busted
Let’s take a quick look at the four common myths surrounding the zero-trust framework and dispel them with facts:
Myth #1: I can achieve zero trust for my business by using a zero-trust product.
Fact: There are no miracle zero-trust solutions. Zero trust is a security strategy that needs to be implemented systematically. However, you can use solutions and tools to support the framework. Consider taking the help of an IT security provider to identify and implement the solutions best suited for your business.
Myth #2: Zero trust is too complicated for me to implement.
Fact: It can be challenging for businesses with limited knowledge or resources to achieve a zero-trust security framework. However, if you lack expertise, consider taking the help of a trusted IT service provider. An IT service provider can help you understand your business’s risk profile and develop a realistic roadmap to implement a comprehensive and effective zero-trust security strategy.
Myth #3: Zero trust will make it difficult for my employees to do their jobs and negatively impact productivity and morale.
Fact: It enables a better user experience and promotes increased collaboration. However, there are always chances for increased friction and decreased efficiency due to the additional security layers. That’s where an IT service provider can help by suggesting user-friendly policies and easy-to-use solutions that balance security with convenience so your employees can perform their jobs seamlessly.
Myth #4: Implementing zero trust is too expensive.
Truth: Implementing zero trust can be expensive, but that cost is still less compared to the fortune you may have to shell out in the event of a major cybersecurity incident. You may have to deploy additional resources and tools to get the best out of a zero-trust security model. However, you can control the expenses and increase efficiency by opting for an IT service provider.
The time to act is now
By now, it must be clear that zero trust is a great security framework to adopt if you want to protect your business against cyberattacks while ensuring business continuity in the event of a breach. However, implementing zero trust on your own can be a challenge. That’s why partnering with a specialist like us would be the best option. Reach out to us to learn how you can leverage our expertise to implement an efficient zero-trust model with minimal effort.
The time to act is now. Start your journey today to a more secure future for your business with a zero-trust security model. To dive deeper into the concept, download our checklist — How to Achieve Zero Trust Security? It is a valuable resource that can help you effortlessly get started with zero-trust security.
3 Steps to Zero Trust Cybersecurity for Small Businesses
Cyberattacks have become rampant and have also grown in sophistication. A simple lapse in your network security could lead to a chain of events that could prove catastrophic for your business. You can avoid this by implementing a robust cybersecurity framework such as zero trust.
Zero trust asserts that no user or application should be trusted automatically. It encourages organizations to verify every access while treating every user or application as a potential threat. Zero trust is a great starting point for businesses that want to build formidable cybersecurity. It can not only adapt to the complexity of the modern work environment, including a hybrid workplace, but also protect people, devices, applications and data irrespective of where they are located.
However, zero trust should not be mistaken for a solution or a platform, regardless of how security vendors market it to you. You can't just buy it from a security vendor and implement it with a click of a button. Zero trust is a strategy — a framework that needs to be applied systematically.
Implementing zero trust: Three core principles to remember
As you begin your journey to implement a zero-trust framework to bolster your IT security, there are three core principles that you must remember:
1, Continually verify
You should strive to implement a “never trust, always verify” approach to security by continuously confirming the identity and access privileges of users, devices and applications. Consider implementing strong identity and access (IAM) controls. It will help you define roles and access privileges — ensuring only the right users can access the right information.
2. Limit access
Misuse of privileged access is one of the most common reasons for cyberattacks. Limiting access ensures that users are granted minimal access without affecting their day-to-day activities. Here are some common security practices that organizations have adopted to limit access:
- Just-in-time access (JIT) – Users, devices or applications are granted access only for a predetermined period. This helps limit the time one has access to critical systems.
- Principle of least privilege (PoLP) – Users, devices or applications are granted the least access or permissions needed to perform their job role.
- Segmented application access (SAA) – Users can only access permitted applications, preventing any malicious users from gaining access to the network.
3. Assume breach and minimize impact
Instead of waiting for a breach, you can take a proactive step toward your cybersecurity by assuming risk. That means treating applications, services, identities and networks — both internal and external — as already compromised. This will improve your response time to a breach, minimize the damage, improve your overall security and, most importantly, protect your business.
We are here to help
Achieving zero trust compliance on your own can be a daunting task. However, partnering with an IT service provider like us can ease your burden. Leverage our advanced technologies and expertise to implement zero trust within your business — without hiring additional talent or bringing on additional tools yourself.
Download our infographic “Why Now Is the Time to Embrace Zero Trust” to learn actionable steps you can take today to build a solid zero trust security framework. Contact us for a no-obligation consultation.
The final curtain call for Windows 10: What you need to know
Microsoft has announced that the current version of Windows 10, released in 2022, will be its final release.
If you’re currently using Windows 10, you might wonder what this means for your day-to-day operations.
The good news is that your computers won’t suddenly stop working. The current updates and security patches for Windows 10 won’t disappear anytime soon either.
However, you may want to consider upgrading to Windows 11 sooner rather than later. Microsoft has made it clear that it will be devoting all its attention to the new operating system from now on, so future developments and innovation will be focused on Windows 11.
Upgrading can be a daunting task, but moving to Windows 11 has so many benefits:
Enhanced performance
Windows 11 has been designed to maximize efficiency and performance across all types of devices, making it a no-brainer for businesses looking for faster and more efficient technology.
Improved user experience
The interface has been updated with a more modern look, making it easier to navigate and customize.
Increased security
Windows 11 comes with Microsoft’s most advanced security features, making it harder for cyber criminals to breach your system.
Better integration with cloud services
Windows 11 gives you access to a range of cloud-based services, making it easier to collaborate with other team members and enhance your business’ productivity.
If you’re still hesitant about upgrading, keep in mind that Microsoft will eventually stop releasing security updates for Windows 10. We’re expecting it to be in late 2025. This means staying with Windows 10 for too long could put your business at risk of security threats.
The sooner you upgrade, the better your protection against these threats, and the more significant the benefits you’ll be able to reap from Windows 11.
Like any big project, making the move to Windows 11 needs to be planned and implemented properly. Your hardware needs to meet certain requirements and, of course, you’ll need to make sure it’s done without affecting day to day operations.
If you’d like help making the transition with as little disruption as possible, get in touch.
Published with permission from Your Tech Updates.
Windows 11 optional update: Why it’s better to wait
Microsoft has just announced an option for people to trial new features before their general release in Windows 11.
This isn’t about fixes to security flaws – everyone gets those at the same time.
This is an opportunity for businesses to jump the queue to receive new features and updates first.
Sound exciting?
Yes!
Worth the risk?
Not quite.
Our advice?
Patience is a virtue!
Sure, it may be tempting to give in to the tantalizing prospect of new features… nobody ever wants to wait. But jumping aboard any trial phase comes with risks.
Bugs, errors, and other stumbling blocks could have a significant impact on your operations, potentially causing chaos in your daily workflow.
Waiting until features have completed a thorough trial process gives you the advantage of other people’s experience. They’ve already dealt with the complexities so, by the time you get the new features, they’ll be polished and dependable. And isn’t that more important for the smooth running of your business?
Trust us, the safe road is the smart road, especially when your business systems are involved. The benefits of being an early adopter may seem enticing, but you don’t want to end up being the guinea pig.
Remember the old adage… good things come to those who wait!
We’re all for keeping up with the latest technology and software updates, but there is a time to exercise caution, and this is one of those times. Don’t be tempted by the shiny new features.
Be patient
Stay safe
And ensure that when the time comes, you’re getting something that’s proven to work
Microsoft already has a lot of (tested and approved) features that can boost productivity and make your work processes smoother. We spend a lot of time helping businesses find the right ones for them. If we can do the same for you, get in touch.
Published with permission from Your Tech Updates.
Can your business go green by switching to the cloud?
Cloud computing has quickly become a popular option for businesses that want to streamline their operations, reduce costs, and become more flexible.
But are you swayed by the idea that cloud services are automatically better for the environment? Could the need to do your bit ‘cloud’ your decision-making?
Sorry. Bad pun.
It’s true that cloud services have environmental benefits compared to using your own servers. These include reduced energy consumption and a smaller carbon footprint.
Yet you shouldn’t view the cloud as a “green solution” without fully understanding the environmental impact.
One consideration of using cloud services is the location of the data centers where servers are housed. Some providers have made commitments to use renewable energy, but it’s not a guarantee. It is essential to do your research and choose a provider that sources renewable energy and uses energy storage where possible.
When thinking about switching to the cloud, there are other benefits besides environmental sustainability. They include improved data security, ease of collaboration, and scalability as your business grows.
Another key advantage of cloud computing is data backup and recovery.
With all your data stored in the cloud, the risk of data loss due to equipment failure, damage, or theft is virtually eliminated. It means that in the event of an unforeseen disaster, like a fire or natural disaster, you can rest assured your data is safe and can be quickly recovered.
Cloud computing also enables better collaboration and communication, helping your team to work together more easily and efficiently, no matter where they’re working from. This can increase productivity and reduce your costs in comparison to maintaining traditional on-site systems.
Finally, cloud services provide better scalability as you grow, with the ability to increase storage and processing power as needed.
Can you see the benefits of cloud computing are huge? It’s why so many businesses have already ditched their servers.
If you’re considering migrating, get in touch – we can talk you through the process and what happens when.
Published with permission from Your Tech Updates.
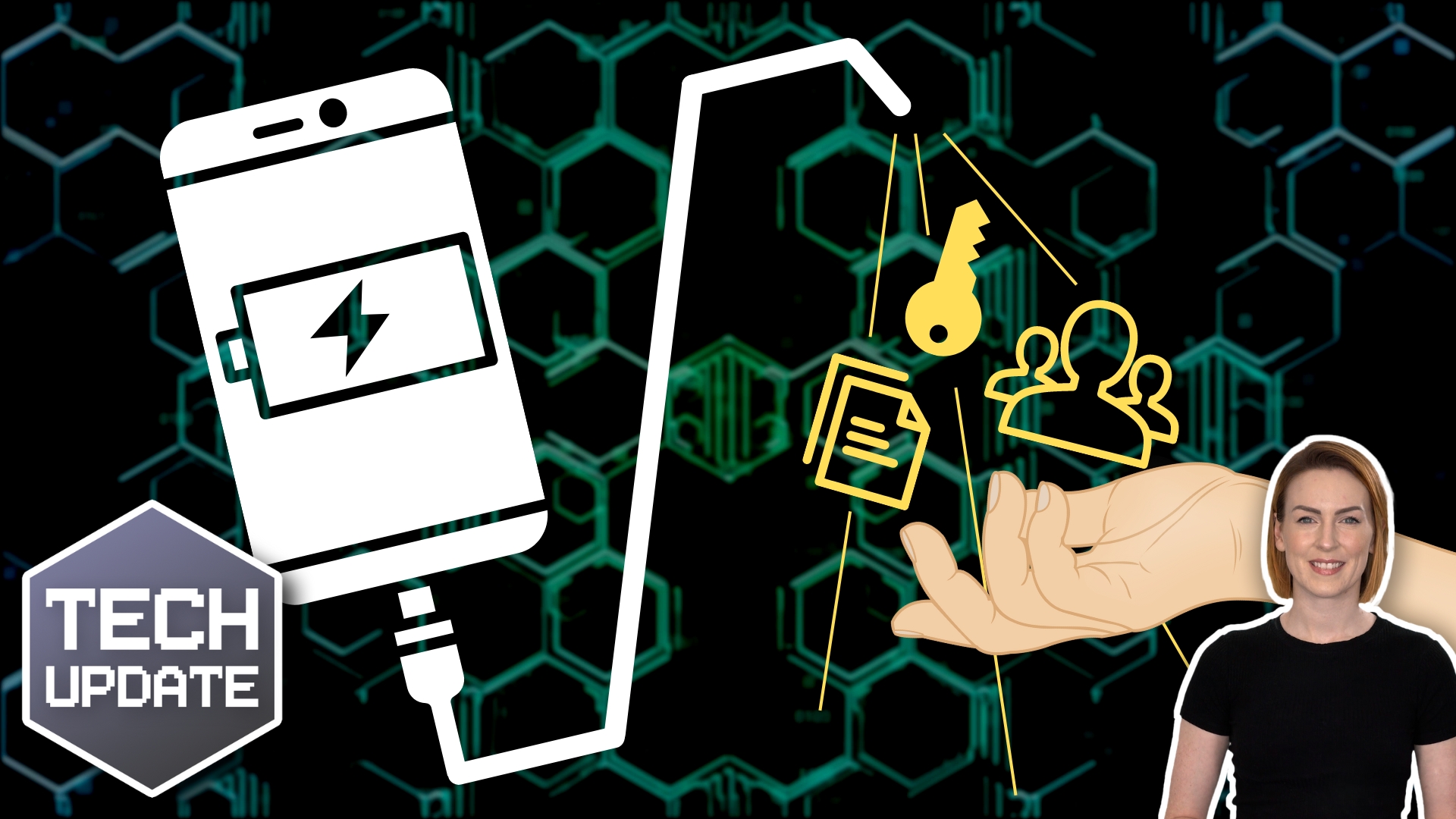
Charging in public places? Watch out for “juice jacking”
Airports, hotels, cafés, even shopping malls, offer public charging points where you can boost your phone or laptop battery on the go.
They’ve been in the news after the FBI recently tweeted advice to stop using them. Crooks have figured out how to hijack USB ports to install malware and monitoring software onto devices as they charge.
The security risk of “juice jacking” was long thought to be more theoretical than real, but the tech needed to carry out an attack has gotten smaller and cheaper and easier to use. This means less sophisticated criminals are now turning their hand to it.
So how does it work?
The most common charging cables – USB-C and lightning – are dual-purpose. They have pins for charging and pins for data.
When you charge your device, you only use the charging pins. But a compromised charging port – or a cable that someone has left behind – could use both charging pins and data pins without you knowing.
When they use the data pins, criminals can install malware onto your device that gives them access to your credentials and other data. It’s a little like plugging your phone into someone else’s laptop.
To avoid the risk, the best solution is to always carry your own charger and cable, and plug it into a power outlet. If you have no choice but to use a public USB port, invest in something called a USB data blocker. This prevents data being transferred, but the device will still charge.
We help businesses stay secure and productive at the same time.
If we can help you, get in touch.
Published with permission from Your Tech Updates.
LinkedIn takes action to tackle fake accounts
LinkedIn is introducing new verification features over the coming months to help tackle fake accounts.
The business-focused social platform is a fantastic place to connect with like-minded businesspeople, and to find new employees, jobs and opportunities.
But thanks to this popularity, we’re seeing an increase in fake profiles, created by scammers for more sinister purposes.
Bot-like accounts have been cropping up all over the platform. They’ve been spamming people, tricking genuine profiles into downloading malware, and scamming them into giving away personal data.
LinkedIn holds a huge amount of information on each of its members, including their job history, contact details, professional interests and places of work – all valuable data that a determined criminal could put to use.
These fake accounts can be hard to spot. They look like real people (sometimes they’re AI-generated deepfake images), they seem to work for legitimate businesses, and the profiles have been carefully curated to look like the real deal.
LinkedIn is making changes over the coming months to help tackle these fake accounts, by way of an improved account authentication process.
Microsoft, which owns LinkedIn, is partnering with secure identity platform Clear to help verify accounts using work email addresses, government-issued ID, and a phone number.
It’s initially only being tested in the US, but if it’s a success, we expect we’ll see a wider rollout over the coming months.
Once the relevant information has been provided, accounts will receive a verification mark, like the ones introduced by Twitter. However, unlike Twitter, LinkedIn will be offering verification free of charge.
We’ll keep you updated when we know more, but in the meantime, if you need help keeping all your accounts secure, get in touch.
Microsoft hints at some exciting Windows 12 developments
We’re fickle creatures.
Windows 11 still feels like a new toy, yet we’ve already heard (reliable) speculation about Windows 12 arriving as soon as next year. And now it’s all we can think about!
What will it look like?
What improvements will we see?
Will there be new features?
We can’t answer these questions with certainty just yet, but there are whispers of new features that could be big news for businesses.
Three in particular have got us excited.
First (and probably most obvious) is the inclusion of more AI functionality. From automation to chatbots, AI has exploded in recent months. It just makes sense that Microsoft will harness this power to bring us a more impressive operating system.
We’re likely to see better AI analysis of our content, and prompts to help us begin projects or choose apps to help get things done. It will also help us speed up what we’re doing with improved intuition for what we’ll do next.
We do know that Microsoft wants to bring us faster updates and better security.
It’s likely things will be split into different sections rather than having the entire OS as a single entity as it stands today. That means updates to different elements will be able to run in the background while you continue to work, and different people may be granted access to each partition for improved security.
Microsoft also intends to make the Windows 12 experience more modular. The benefit of creating different components in this way is that higher-powered devices will get the maximum Windows experience, while lower-powered devices will still be able to do everything they need, running the Edge browser, Office tools, or web apps, for instance.
Some of these features may be reliant on dedicated hardware and upgraded equipment and we’re waiting for more announcements on that. As soon as we hear, you’ll be the first to know!
If you haven’t yet made the move to Windows 11, now’s a good time. Get in touch if you need any help or advice.
Criminals are exploiting AI to create more convincing scams
One of the many cool things about the new wave of Artificial Intelligence tools is their ability to sound convincingly human.
AI chatbots can be prompted to generate text that you’d never know was written by a robot. And they can keep producing it – quickly, and with minimal human intervention.
So it’s no surprise that cyber criminals have been using AI chatbots to try to make their own lives easier.
Police have identified the three main ways crooks have found to use the chatbot for malicious reasons.
1. Better phishing emails
Until now, terrible spelling and grammar have made it easy to spot many phishing emails. These are intended to trick you into clicking a link to download malware or steal information. AI-written text is way harder to spot, simply because it isn’t riddled with mistakes.
Worse, criminals can make every phishing email they send unique, making it harder for spam filters to spot potentially dangerous content.
2. Spreading misinformation
“Write me ten social media posts that accuse the CEO of the Acme Corporation of having an affair. Mention the following news outlets”. Spreading misinformation and disinformation may not seem like an immediate threat to you, but it could lead to your employees falling for scams, clicking malware links, or even damage the reputation of your business or members of your team.
3. Creating malicious code
AI can already write pretty good computer code and is getting better all the time. Criminals could use it to create malware.
It’s not the software’s fault – it’s just doing what it’s told – but until there’s a reliable way for the AI creators to safeguard against this, it remains a potential threat.
The creators of AI tools are not the ones responsible for criminals taking advantage of their powerful software. ChatGPT creator OpenAI, for example, is working to prevent its tools from being used maliciously.
What this does show is the need to stay one step ahead of the cyber crooks in everything we do. That’s why we work so hard with our clients to keep them protected from criminal threats, and informed about what’s coming next.
If you’re concerned about your people falling for increasingly sophisticated scams, be sure to keep them updated about how the scams work and what to look out for.
If you need help with that, get in touch.
Top 9 Benefits of Outsourcing Your Cybersecurity
When it comes to protecting your business from cyberthreats, having the right tools and technology is only half the battle. You also need the expertise, controls and processes to manage and mitigate these threats effectively. That’s where a managed security service provider (MSSP) comes in.
Think of a Managed IT Service Provider as your outsourced cybersecurity department, ensuring your technology is safe, secure and compliant.
In this article, we discuss the benefits of outsourcing your cybersecurity to a trusted MSSP partner. From enhanced security posture to cost savings, you’ll learn how collaborating in cybersecurity matters can help protect your business from cyberthreats while streamlining your IT operations.
The benefits of outsourcing your cybersecurity
Although there are a lot of benefits to outsourcing your cybersecurity, we’re listing the top nine below:
Enhance business outcomes
Partnering with a Managed IT Service Provider can help you enhance your business outcomes by reducing downtime, increasing productivity and improving customer satisfaction. You can focus on growing your business and achieving your strategic goals by mitigating cyberthreats and keeping your IT systems secure.
Fill IT gaps
A Managed IT Service Provider can help fill IT gaps by providing the expertise, controls and processes to manage and mitigate cyberthreats. Whether it’s managing vulnerabilities, implementing security controls or responding to incidents, a Managed IT Service Provider can help you bridge the gaps in your IT security.
Lower costs
Outsourcing your cybersecurity to a Managed IT Service Provider can also help you lower costs. Instead of investing in expensive cybersecurity tools and technologies, you can leverage a Managed IT Service Provider’s expertise and infrastructure to achieve the same level of security at a fraction of the cost.
Access to specialized, experienced security experts
A Managed IT Service Provider has a team of specialized, experienced security experts who can provide the support and guidance you need to manage and mitigate cyberthreats effectively. These experts have the knowledge and expertise to rapidly implement advanced security solutions and respond to incidents.
Advanced security solutions
Partnering with a Managed IT Service Provider also gives you access to advanced security solutions that may otherwise be unavailable. From threat intelligence and hunting to endpoint protection and cloud security, a Managed IT Service Provider can provide you with the latest security solutions to keep your IT systems safe and secure.
Rapid incident response and remediation
In the event of a cyberattack, a Managed IT Service Provider can provide rapid incident response and remediation services. Their experts can quickly identify and isolate the threat, contain the damage and restore your IT systems to full functionality, minimizing downtime and reducing the impact on your business.
Ongoing, continuous protection
Cyberthreats are constantly evolving, so it’s essential to have ongoing, continuous protection in place. A Managed IT Service Provider can provide you with the 24/7 monitoring and management needed to detect and mitigate cyberthreats in real-time, ensuring your IT systems are always protected.
Threat intelligence and hunting
A Managed IT Service Provider can also provide you with threat intelligence and hunting services, which involve monitoring and analyzing threats in real-time to identify potential vulnerabilities and prevent attacks before they occur.
Compliance support
Finally, partnering with a Managed IT Service Provider makes meeting your compliance requirements easier. A Managed IT Service Provider can provide the support and guidance needed to comply with industry-specific regulations, such as HIPAA, PCI DSS and GDPR, and ensure that your IT systems are always compliant and secure.
Partner to succeed
Outsourcing your cybersecurity needs to a Managed IT Service Provider is an investment to secure the future of your business. The benefits of enhanced business outcomes, filling IT gaps, lower costs and more make it a wise choice for any organization looking to strengthen its security posture.
By partnering with a Managed IT Service Provider like us, you’ll get the expertise and experience to protect your business from ever-increasing, sophisticated cyberthreats. Don’t wait until it’s too late. Contact us now to bolster your cybersecurity.